Security Plan Templates (SDLC)
$9.99
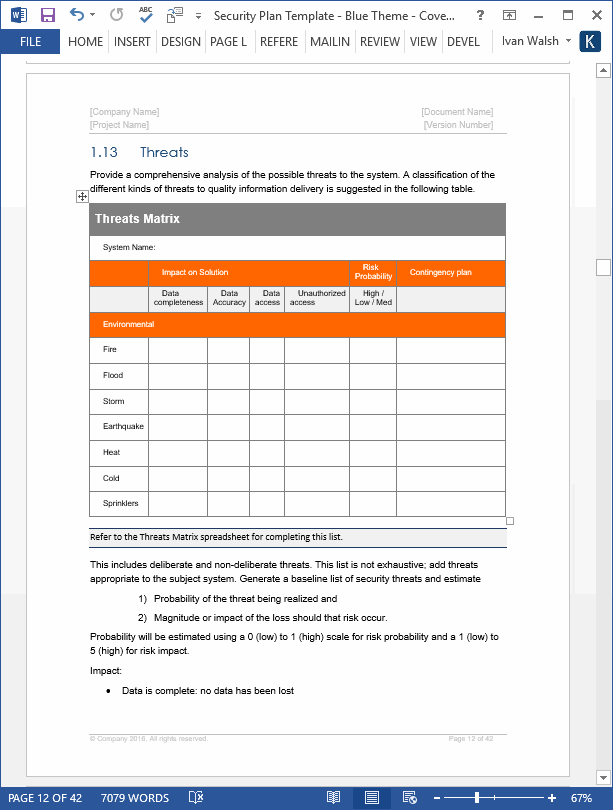
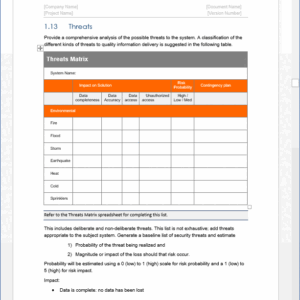
This 25 page Word template and 7 Excel templates including a Threats Matrix, Risk Assessment Controls, Identification and Authentication Controls, Controls Status, Access Control Lists, Contingency Planning Controls, and an Application Inventory Form.
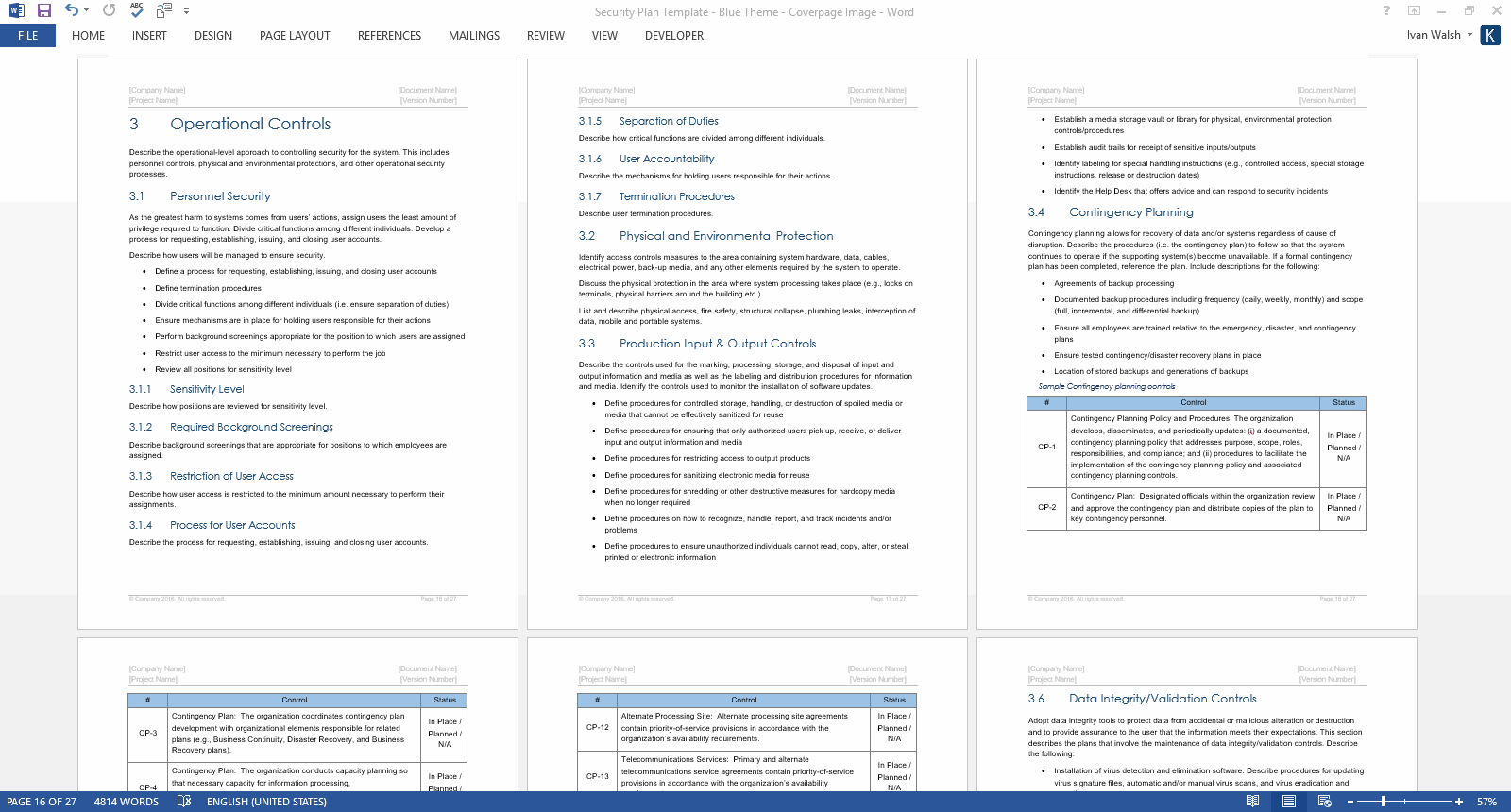
Review security controls when system modifications are made. Reduce security vulnerabilities related to systems configurations. Provide guidelines to establish system security & privacy requirements.
This 25 page Word template and 7 Excel templates including a Threats Matrix, Risk Assessment Controls, Identification and Authentication Controls, Controls Status, Access Control Lists, Contingency Planning Controls, and an Application Inventory Form.
Use this template to:
- Review security controls when system modifications are made.
- Eliminate security vulnerabilities related to systems configurations.
- Implement uniforms security controls across systems and databases.
- Identify penalties for different levels of security breaches.
Related products
Maintenance Phase
Planning Phase
Maintenance Phase
Development Phase
Development Phase
Development Phase
Deployment Phase
Deployment Phase